SOC 2 Compliance
A Guide for Service Providers
Contents
Introduction
In today’s data-driven world, where trust is paramount, service providers must ensure they are handling client data with the highest level of security and confidentiality. For service providers, SOC 2 compliance has become one of the most crucial standards in the industry. SOC 2 (System and Organization Controls 2) is a framework established by the American Institute of Certified Public Accountants (AICPA) to evaluate how well a company performs in areas such as security, availability, processing integrity, confidentiality, and privacy.
For businesses offering services that involve handling sensitive data, such as cloud computing, SaaS, IT services, and more, SOC 2 compliance is vital for gaining and retaining clients. Non-compliance can lead to a loss of client trust, damage to your reputation, and, in some cases, legal ramifications. At Data Collaboration Services (DCS), we understand the critical nature of SOC 2 compliance and help our clients align their operations with these rigorous standards. While DCS does not offer direct SOC 2 certification services, we provide consulting and guidance to ensure you are on the right track toward SOC 2 compliance.
What is SOC 2?
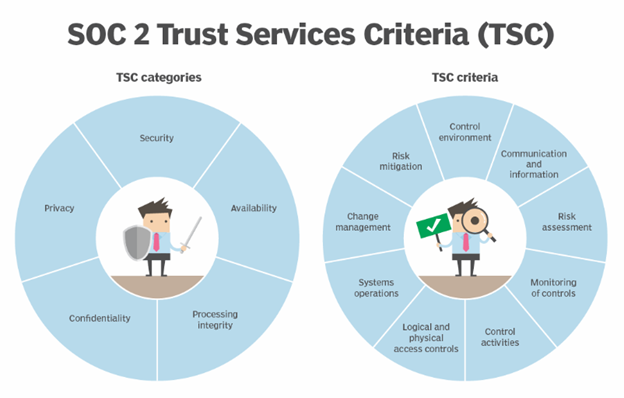
SOC 2 was created to assess how well a service organization handles data to ensure it is protected in five key areas known as the Trust Services Criteria (TSC):
- Security: How well is the data protected against unauthorized access?
- Availability: Is the service accessible as promised or agreed upon?
- Processing Integrity: Are systems processing data accurately, completely, and on time?
- Confidentiality: Is the data kept confidential, as agreed upon with clients?
- Privacy: Is personal data collected and used in accordance with privacy regulations?
SOC 2 reports are issued by an independent auditor after they assess a service provider’s controls in each of these areas. The report will help clients evaluate the risks involved in engaging with a service provider.
Why SOC 2 Compliance is Crucial for Service Providers
SOC 2 compliance is critical for service providers for several reasons, especially those handling sensitive customer data. Here’s why it matters:
1. Build Customer Trust
SOC 2 compliance shows your commitment to data security and privacy. By having a SOC 2 report, you provide tangible proof to your customers that their data is being protected with the highest level of care. This builds trust with potential and existing clients, making them more likely to engage with your business.
2.Meet Client Requirements
Many companies, especially those in industries like finance, healthcare, and e-commerce, require their vendors to be SOC 2 compliant before they can be trusted with sensitive data. In fact, having a SOC 2 report may be a prerequisite for entering certain markets or partnerships.
3.Reduce the Risk of Data Breaches
SOC 2 compliance ensures you have controls in place to prevent unauthorized access to sensitive data, reducing the risk of data breaches that could lead to fines, reputational damage, or customer lawsuits.
4.Stay Ahead of Regulatory Compliance
SOC 2 can help you stay ahead of evolving regulations related to data privacy and security, such as GDPR, CCPA, and others. Complying with SOC 2 is an effective way to ensure your business meets the latest security and privacy requirements.
5.Competitive Advantage
SOC 2 compliance can also act as a differentiator in the marketplace. Clients prefer to work with service providers who are transparent about their security practices and who demonstrate their commitment to protecting client data. By obtaining SOC 2 certification, you can stand out in a competitive industry.
How DCS Can Guide You Through SOC 2 Compliance
At DCS, we are not a SOC 2 certification provider, but we are well-equipped to guide businesses through the necessary steps to achieve compliance. We offer consulting services to help you align your processes with SOC 2 standards, ensuring that your company meets the security, privacy, and confidentiality requirements expected of service providers.
Here’s how DCS can assist you in navigating SOC 2 compliance:
1. Conducting a Gap Analysis
The first step to achieving SOC 2 compliance is understanding where your current practices stand in relation to SOC 2’s Trust Services Criteria (TSC). We can help you identify gaps in your systems, policies, and procedures that need to be addressed. This analysis will give you a clear roadmap to implement the necessary improvements.
2.Help with Privacy and Security Frameworks
SOC 2 emphasizes strong security controls and privacy policies. DCS can guide you in implementing privacy-by-design and security-by-design frameworks that prioritize confidentiality, data access management, and secure data storage and transmission.
3.Assist in Process Optimization
SOC 2 mandates businesses to establish efficient and secure processes for handling customer data. We can help optimize your processes to meet SOC 2’s requirements, including enhancing your data handling workflows, improving data integrity, and ensuring proper access controls.
4.Provide Support for Vendor Management
Since SOC 2 requires businesses to assess third-party vendors for their security and privacy practices, DCS can help you create and implement vendor risk assessments and contracts to ensure your third-party partners meet the SOC 2 standards.
5.Guide Your SOC 2 Readiness for Audits
Although we do not offer SOC 2 certification services, we provide critical assistance in preparing your business for the official audit. Our team can help ensure that your documentation is in place, security controls are implemented, and the data flows through your organization in compliance with SOC 2.
6.Train Your Team on SOC 2 Best Practices
Achieving SOC 2 compliance is not just about implementing controls, it’s also about creating a culture of security and compliance within your organization. DCS offers employee training to help your team understand SOC 2 principles and maintain them consistently in day-to-day operations.
Final Thoughts
SOC 2 compliance is not just a set of standards, it’s a commitment to data security, transparency, and client trust. For service providers, meeting SOC 2 requirements is a critical step toward demonstrating that you are serious about protecting customer data and meeting privacy expectations. At DCS, we help guide businesses through the SOC 2 compliance process by providing consulting and support to help you align with the standards and successfully navigate the requirements.
For more information on how DCS can help ensure your business is SOC 2 compliant and ready to face the future of data protection, contact us.
Frequently Asked Questions (FAQ's)
SOC 2 compliance is a framework designed to ensure that a service provider securely manages its clients' data and protects privacy. It focuses on security, availability, processing integrity, confidentiality, and privacy.
Achieving SOC 2 compliance involves implementing strong security measures, privacy controls, and data management practices that align with the Trust Services Criteria. An independent auditor will assess your controls to ensure they meet the SOC 2 requirements.
We offer consulting and guidance to help your organization prepare for SOC 2 compliance and assist in improving your systems and processes to meet the criteria.
The timeline for SOC 2 compliance varies depending on the complexity of your systems and the gaps that need to be addressed. Typically, the process can take several months to complete, including gap assessments, process improvements, and documentation preparation.
SOC 2 compliance builds trust with your clients, helps you reduce risks related to data breaches, and provides you with a competitive edge by showing that your business is committed to data protection and privacy.
SOC 2 compliance requires your IT systems to have strong security controls in place, including data encryption, access management, and real-time monitoring to ensure data is protected and that your systems are available to clients as agreed.
Although SOC 2 does not impose legal penalties for non-compliance, failing to comply can result in reputational damage, loss of clients, and potential lawsuits for not meeting service agreements and data protection standards.

