Let’s face it, cybersecurity threats are the modern-day bogeymen, and they’re lurking everywhere. Phishing scams, data breaches, and ransomware have become the three biggest nightmares in the world of IT, constantly threatening businesses big and small. It’s no longer just a concern for giant corporations; small businesses are at risk too. Did you know that 43% of cyberattacks target small businesses? That’s right, you’re not off the hook just because you’re not a multinational.
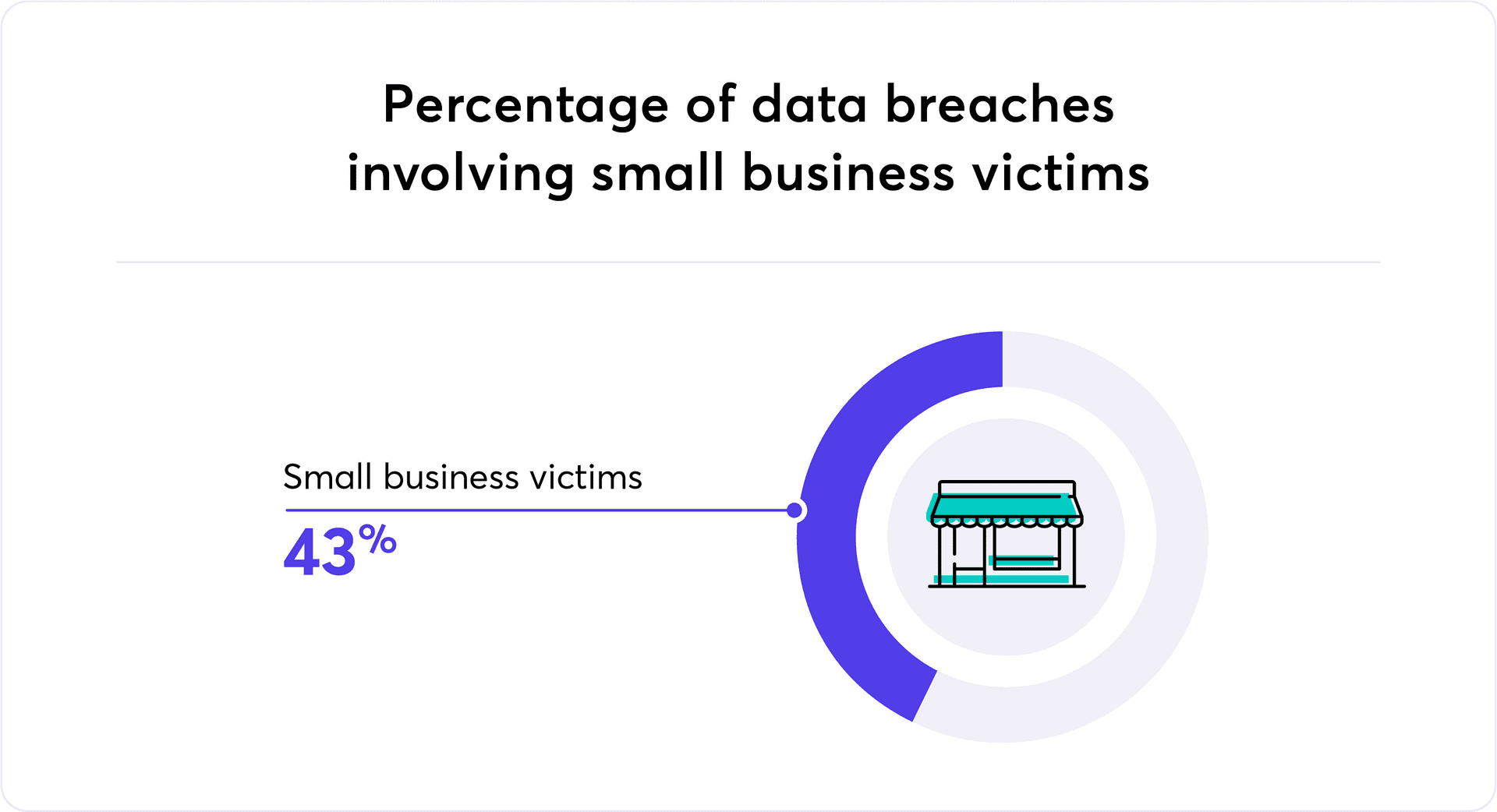
Source: Business News Daily
Phishing: The sneaky emails that look like they’re from your bank or someone you trust.
Data breaches: That terrifying moment when hackers get their hands on your sensitive data.
Ransomware: The nightmare where your data is hijacked and held hostage until you pay up.
But, here’s the good news: You don’t have to live in fear! With a little know-how and the right cybersecurity services partner, you can protect your business.
In this guide, we’ll explore how to prevent phishing scams, data breaches and ransomware. Ready to kick those hackers to the curb? Let’s get started.
Understanding Cybersecurity Threats
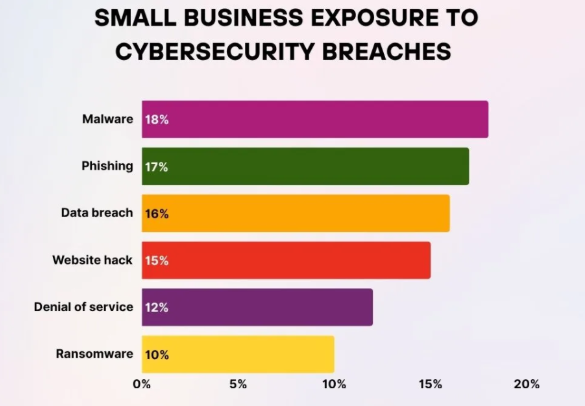
Source: SQ Magazine
Phishing Scams
Ah, phishing! The sneakiest of the bunch. Imagine you get an email that looks like it’s from your bank, asking you to verify your account information. You’re in a rush, so you click the link. Oops. It was a fake link, and now your login credentials are in the hands of cybercriminals. That’s phishing in a nutshell.
The most common initial access methods in 2024 include:
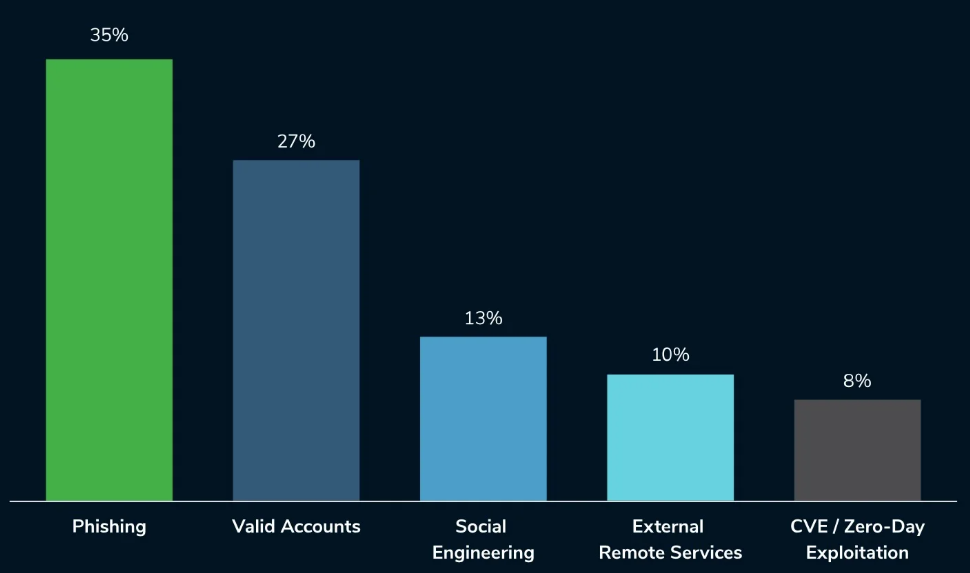
Source: Help Net Security
Common Methods Used in Phishing Scams:
- Email Phishing: Fake emails asking you to click on malicious links.
- Spear Phishing: Personalized emails targeting a specific person or company.
- Vishing: Phone calls impersonating trusted sources to steal sensitive info.
- Smishing: Texts that lure you into providing personal data.
Real-World Example: Remember the 2016 Democratic National Committee hack? A phishing email disguised as a Google Docs link gave hackers access to thousands of emails. If they can trick a political powerhouse, your company’s email isn’t immune!
Did you know?
According to a report, over 30% of all data breaches involve phishing.
Data Breaches
A data breach is like a burglar breaking into your house and taking your most valuable items, only in this case, it’s your sensitive information. Whether it’s customer data, intellectual property, or financial details, once a breach occurs, it’s a setback for your reputation.
Source: TechTarget
What Constitutes a Data Leak?
A data leak happens when sensitive information is accidentally or maliciously exposed to unauthorized individuals. This can happen when files are sent to the wrong email address or due to unsecured databases.
Common Causes of Data Breaches:
- Weak passwords (yep, “password123” is not a good idea)
- Vulnerabilities in your software
- Poor encryption
- Human error (like an employee mistakenly sending confidential files to the wrong recipient)
Ransomware
Ransomware is the cybercriminal’s ultimate extortion tool. It locks your data and demands a ransom usually in cryptocurrency to release it.
How Ransomware Spreads:
- Phishing emails (yep, phishing again!)
- Unpatched vulnerabilities in your software
- Malicious websites or downloads

Source: GeeksforGeeks
Did you know?
Global ransomware attacks are estimated to cost businesses $20 billion annually, according to Cybersecurity Ventures. That’s a serious number!
Preventing Phishing Scams
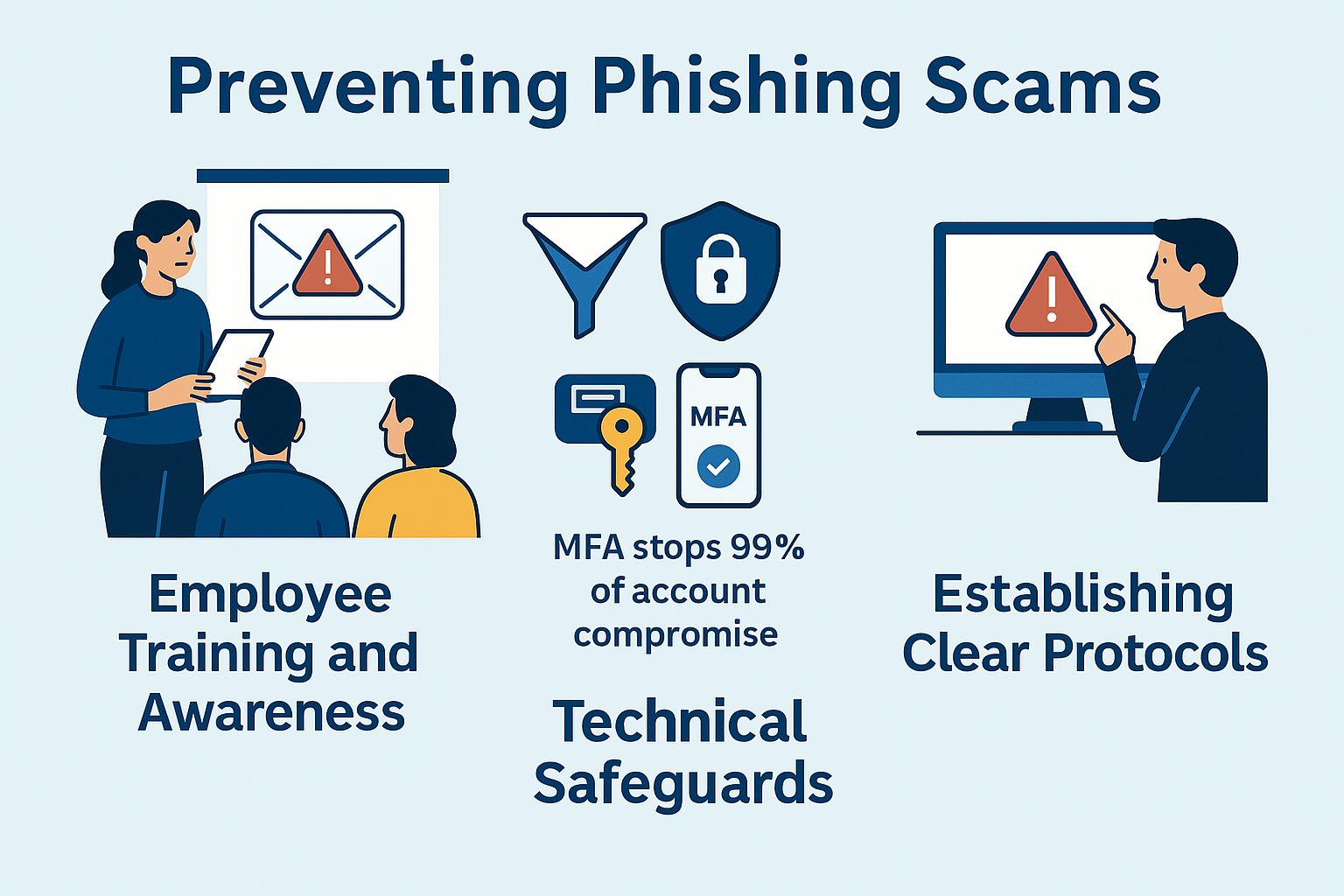
Employee Training and Awareness
Training your employees to spot phishing attempts is crucial. More than 80% of data breaches involve human error, so having well-trained staff can drastically reduce your risk.
What Should Training Cover?
- Recognizing suspicious emails: Do they look legitimate? Are there spelling errors?
- Verifying strange requests: Is someone asking for sensitive data unexpectedly?
- Phishing simulations: Run regular drills to test your employees.
Implementing Technical Safeguards
Get your tech team to set up anti-phishing tools and email filters to block malicious emails before they hit your inbox. Also, implementing multi-factor authentication (MFA) is a game-changer. It adds an extra layer of protection to your logins.
Did you know?
Companies that use MFA are 99% less likely to be compromised in phishing attacks.
Establishing Clear Protocols
Create company-wide protocols for handling suspicious emails, including:
- Reporting phishing emails to the IT department.
- Blocking access to dangerous links.
- Conducting regular phishing audits to test your team’s readiness.
Safeguarding Against Data Breaches
Data Encryption
Encrypt your sensitive data both at rest and in transit. This means even if data is intercepted, it will be unreadable to unauthorized individuals. AES-256 encryption is considered one of the strongest standards.
Access Controls
Ensure that only authorized personnel have access to sensitive data. Role-based access control (RBAC) allows you to assign specific permissions based on job roles, so employees only access the data they need.
Best Practices:
- Review access rights regularly.
- Implement strong authentication methods.
Data Loss Prevention (DLP) Tools
DLP tools monitor your network for unauthorized data transfers. By setting up DLP solutions, you can prevent sensitive information from being exfiltrated.
Modern DLP technologies work across endpoints, networks, and cloud platforms to detect and block unauthorized data transfers. They’re especially vital for organizations handling confidential client data, financial records, or regulated information. DLP tools stop suspicious activity like copying sensitive files to USB drives or sending them via unsecured email.
Case Study: How we helped a Manhattan Financial Firm Cut Cybersecurity Costs
These tools continuously monitor your network and devices for unusual data activity, identifying attempts to move or share information outside approved channels. For example, if an employee tries to upload a confidential file to a personal Google Drive, the DLP system can instantly block it and alert the administrator. It’s like having a smart security guard that never takes a lunch break.
DLP tools seamlessly integrate with your organization’s existing IT infrastructure, including email servers, endpoint devices, and cloud storage systems such as Microsoft 365 or Google Workspace. This unified approach ensures visibility across your entire digital environment. When combined with your cybersecurity stack (firewalls, endpoint protection, and SIEM tools), DLP adds an extra layer of data defense that’s proactive, not reactive.
You may also like to read: Why Cyber Security Solutions are Important
Defending Against Ransomware

Regular Backups
Data backups are your safety net in case ransomware strikes. Keep your backups offline or in the cloud and test restoration regularly. This ensures you can recover data quickly and avoid paying the ransom.
Network Segmentation
Network segmentation is like creating firewalls within your own systems. It prevents ransomware from spreading across your entire network if it manages to slip past the outer defenses.
Incident Response Planning
Develop an incident response plan specifically for ransomware. This plan should include:
- Isolating infected systems.
- Notifying stakeholders and customers.
- Restoring from backups.
You may also like to read: The Ultimate Guide to IT Disaster Recovery Planning
The Role of Cybersecurity Services
Managed Security Service Providers (MSSPs)
A Managed Security Service Provider (MSSP) is like having a full-time cybersecurity team without the overhead. They monitor, detect, and respond to threats 24/7, so your business stays secure, even while you sleep.
Why MSSPs Matter:
- 24/7 Protection: Continuous threat monitoring, penetration testing and quick incident response.
- Expertise on Demand: Access to certified cybersecurity experts and cutting-edge tools.
- Compliance Support: MSSPs help you stay ahead of complex regulations like HIPAA, GDPR, and NYDFS 23 NYCRR 500.
With the cyber threat landscape evolving daily, partnering with an MSSP ensures your defenses evolve too.
Cyber Threat Intelligence
In cybersecurity, knowledge truly is power. Cyber threat intelligence (CTI) means collecting and analyzing data about current and emerging threats from phishing campaigns to ransomware strains, so you can respond before an attack hits.
How CTI Helps Your Business:
- Identifies new vulnerabilities and attack patterns.
- Strengthens proactive defense strategies.
- Keeps you ahead of cybercriminals, not behind them.
Integrating CTI into your security operations helps transform your defenses from reactive to predictive.
Compliance and Regulatory Considerations
Meeting cybersecurity compliance requirements isn’t just about checking boxes, it’s about building trust and protecting your data. Regulations like GDPR, HIPAA, and CCPA set the foundation for secure data handling.
Steps to Stay Compliant:
- Conduct regular network security audits and risk assessments.
- Implement access controls and encryption aligned with regulatory frameworks.
- Work with a trusted cybersecurity partner that understands your industry’s compliance landscape.
You might also like to read: Common Types of Cybersecurity Threats
Conclusion
Cybersecurity is a marathon, not a sprint. Protecting your business from phishing scams, data breaches, and ransomware requires a proactive, multifaceted approach. From employee training to data encryption, you need to adopt a comprehensive strategy to stay ahead of cybercriminals.
At Data Collaboration Services (DCS), we offer cybersecurity services designed to safeguard your business from these threats. Whether it’s bolstering your security defenses and protocols or ensuring regulatory compliance, we’ve got you covered.
Don’t wait for a breach to make the move! Strengthen your security posture and defenses today with Data Collaboration Services.
Book Your Free Cybersecurity Consultation Now.
Frequently Asked Questions (FAQs)
- What is phishing, and how can I recognize it?
Phishing is a fraudulent attempt to steal sensitive information by impersonating legitimate entities. To spot phishing scams, look for suspicious email addresses, urgent requests, and typos in messages. - How can I protect my business from data leaks?
Conduct threat and penetration testing, encrypt sensitive data, implement strong access controls, and use Data Loss Prevention (DLP) tools to monitor and restrict unauthorized data movements. - What should I do if my organization falls victim to ransomware?
Immediately isolate the infected system, notify stakeholders, and restore from secure backups. - Are there any tools to help prevent phishing attacks?
Yes! Anti-phishing tools like email filtering, multi-factor authentication, and regular employee training can significantly reduce phishing risks. - What is data encryption, and why is it important?
Data encryption secures your sensitive information by making it unreadable without a decryption key. It’s essential for protecting data both in transit and at rest. - How often should I back up my data to prevent ransomware damage?
Back up data regularly (daily or weekly) and store backups in secure locations. Test restoration processes to ensure you can recover quickly if attacked. - What is a Managed Security Service Provider (MSSP)?
An MSSP is a third-party provider that monitors your systems for threats, manages firewalls, and helps ensure your security measures are up to date. - How can I ensure compliance with cybersecurity regulations?
Regular audits, employee training, and adopting industry-standard security protocols will ensure your organization stays compliant with regulations like GDPR and HIPAA. - What are the signs of a potential data breach?
Look for unusual network activity, unauthorized access attempts, missing files, or irregular login behavior. - How can I train my employees to recognize and avoid phishing scams?
Conduct regular cybersecurity awareness training sessions, run phishing simulations, and encourage employees to verify requests for sensitive information.
Take your cybersecurity to the next level! Contact Data Collaboration Services (DCS) today.
Schedule your free IT Security & Compliance Assessment

