You grab your morning coffee, log into your email, and boom, there’s a message that looks like it’s from your bank. The logo’s there, the language sounds legit, and the subject line screams: “URGENT: Account Locked!” Do you click? Do you enter your credentials?
That’s exactly how a phishing email attack works and it’s just one of many ways cyber-criminals try to outsmart businesses every single day.
Here’s the reality: cybersecurity isn’t optional anymore. It’s not just for big tech firms or Fortune 500s. Every business, from a 10-person accounting firm to a growing e-commerce shop, is a potential target. In fact, according to Statista, global cybercrime costs are expected to hit $13.82 trillion by 2028, a 15% year-over-year rise. Let that sink in.
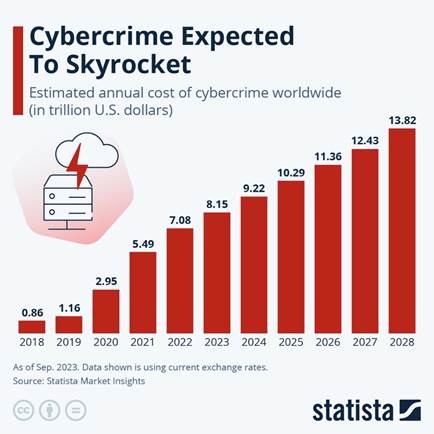
Source: Statista
So the question isn’t if you’ll face a cyber threat, but when. And more importantly, are you ready?
If you want to skip straight to solutions, check out our Cyber Security Services designed to keep businesses like yours safe, secure, and confident.
What’s Driving the Surge in Cyber Attacks?
Cybercriminals aren’t hanging out in basements typing code in the dark anymore. They’re running operations that look more like Fortune 500 companies, only their business model is stealing your data. Here’s why attacks are skyrocketing:
1. Remote & Hybrid Work
Home Wi-Fi is not enterprise-grade firewalls. When employees access sensitive systems from unsecured devices, attackers see an open door.
2. Outdated Systems
Still running Windows 7 somewhere in your office? Legacy systems are a cybercriminal’s playground.
3. Explosion of IoT Device
From smart thermostats to industrial sensors, the Internet of Things has expanded your attack surface dramatically.
4. AI-Powered Attacks
Yep, cybercriminals use AI too. Automated scripts scan for vulnerabilities and mimic user behavior faster than your IT team can blink.
5. Small Businesses = Big Targets
Think you’re “too small to hack”? Think again. Verizon’s Data Breach Investigations Report found that 43% of cyberattacks target small businesses. Why? Because attackers know SMBs often lack proper network security.
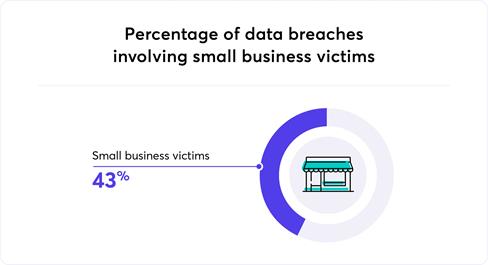
Source: Business News Daily[AS2]
The Most Common Types of Cyber Attacks
To beat the attackers, you’ve got to know the playbook. Here are the big hitters:
- Ransomware Attacks: Criminals lock your files and demand a ransom in Bitcoin. Paying doesn’t guarantee you get your data back.
- Phishing Emails: Fake invoices, “urgent” HR notices, or bogus vendor requests trick employees into handing over data.
- Business Email Compromise (BEC): Hackers pose as your CEO and request a “quick wire transfer.” These scams cost U.S. businesses $2.7 billion in 2022 (FBI IC3).
- DDoS Attacks: Overwhelm your servers with traffic until they crash. Think of it as thousands of bots jamming the entrance to your store.
- Insider Threats: Disgruntled employees or careless contractors can expose data faster than a hacker halfway around the world.
- Zero-Day Exploits: Attackers find a flaw before the software vendor does. By the time a patch is out, damage is done.
You may also like: The Hidden Cyber Risks in Your Out-of-Office Email (And How to Fix It)
The Real Cost of Cyber Attacks
Cyberattacks don’t just mess with your IT, they mess with your entire business:
- Financial Loss: IBM’s Cost of a Data Breach Report 2025 puts the average cost of a breach at $4.45 million.
- Downtime: Every hour your systems are down = lost sales, lost productivity, and angry customers.
- Reputation Damage: Customers don’t forget when their data is leaked. Trust, once broken, takes years to rebuild.
- Legal Trouble: Fail to meet compliance (HIPAA, GDPR, CCPA), and fines follow fast.
- Insurance Premiums: Breach today, higher premiums tomorrow.
How DCS Security Services Keep You Protected
At Data Collaboration Services (DCS), we don’t sell cookie-cutter solutions. We build cybersecurity solutions around your business, your vulnerabilities, and your goals. Here’s how we keep the bad guys out:
- 24/7 Monitoring and Threat Response: Our SOC team watches your network like hawks, keeping an eye on all types of cyber threats. Threat detected? Response in seconds, not hours.
- Next-Gen Firewalls and Endpoint Protection: Every device on your network: laptops, mobile phones, servers, etc., gets enterprise-grade network security and endpoint security.
- Threat and Penetration Testing: Want to know how hackers might break in? We simulate real-world attacks with best-in-class Threat & Penetration Testing and patch the gaps before someone else finds them.
- Network Security Audits: Think of network security audits as health checkups for your IT. Our Network Security Audits uncover weaknesses so you can fix them proactively.
- Data Encryption and Backups: Even if attackers get in, your data is encrypted, locked, and backed up securely in the cloud with our robust Data Backup and Disaster Recovery Solutions.
- Employee Training: We provide cybersecurity awareness training on cybersecurity best practices including phishing simulations, ransomware attack prevention, and password best practices to help your team stay informed and protect against threats.
Why Businesses Choose DCS
- Tailored cybersecurity solutions and plans (built around your actual risks, not generic threats).
- Proactive, not reactive (we stop attacks before they reach you).
- Certified ransomware, phishing, cloud and network security experts (Our team lives and breathes cybersecurity).
- Clear reporting.
- Local NYC roots, national reach (NYC tough, nationwide trusted).
Final Thoughts: Don’t Wait for the Breach!
Cyberattacks aren’t slowing down. They’re getting faster, smarter, and nastier. Waiting until after a breach to act is like buying flood insurance after the hurricane.
The good news? You’re not on your own. With DCS as your cybersecurity partner, you’ll have peace of mind knowing your security defenses and infrastructure are built for today’s threats and tomorrow’s.
Ready to see where your defenses stand? Book a free cybersecurity consultation with our team today. Your future self will thank you.


